Table of Contents
Introduction:
Two-Factor Authentication Setup Guide is essential for anyone looking to add an extra layer of security to their online accounts. With cyber threats increasing every day, relying on just passwords is no longer safe enough. Whether you’re managing your productivity tools like Notion or handling sensitive personal data, securing your accounts with two-factor authentication (2FA) is a must. If you recently read the Notion Review 2025: Is It Still the Best All-in-One Productivity Tool? by Ultimate Product Review, you’ll know how important it is to protect your productivity apps and data. This guide will walk you through easy steps to set up 2FA on your most-used platforms and keep your digital life safe.
What is Two-Factor Authentication and Why You Need It
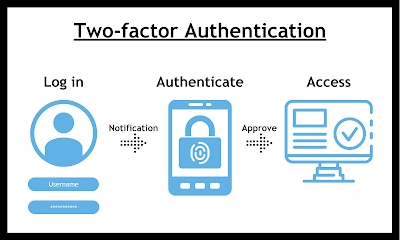
Understanding Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is a security measure that requires users to verify their identity through two distinct factors before gaining access to an account or system. Typically, these factors fall into three categories: something you know (like a password), something you have (like a smartphone or hardware token), or something you are (such as a fingerprint or facial recognition). By combining two of these factors, 2FA adds an extra layer of protection beyond just a password.
Difference Between Single-Factor and Two-Factor Authentication
- Single-Factor Authentication: This is the traditional login method that relies solely on one factor—usually a password or PIN. While convenient, it is vulnerable to attacks if the password is compromised.
- Two-Factor Authentication: In contrast, 2FA requires two separate credentials from different categories, making it significantly more secure. Even if a hacker obtains your password, they would still need the second factor to access your account.
How Two-Factor Authentication Protects You
Two-factor authentication defends against many common cyber threats, including:
- Phishing Attacks: Where attackers trick you into revealing your password. Even if they get your password, 2FA prevents access without the second factor.
- Brute Force Attacks: Automated attempts to guess your password are useless without the second authentication step.
- Keylogging and Data Breaches: If your password is captured or leaked, the additional verification step keeps your account safe.
By implementing 2FA, you dramatically reduce the risk of unauthorized access, helping to keep your personal and professional data secure.
Types of Two-Factor Authentication Methods
SMS-Based Authentication Codes
This is one of the most common and accessible forms of two-factor authentication. After entering your password, a unique code is sent via SMS to your registered mobile phone number. You must then enter this code to complete the login process. While convenient, SMS-based 2FA can be vulnerable to SIM swapping attacks or interception, so it’s best combined with other security practices.
Authentication Apps

Authentication apps like Google Authenticator, Authy, and Microsoft Authenticator generate time-based one-time passwords (TOTPs) that refresh every 30 seconds. Unlike SMS, these apps don’t rely on your mobile network, making them more secure and reliable. You scan a QR code during setup, and the app then provides a constantly changing code to enter along with your password. Many services recommend using authentication apps as a safer alternative to SMS.
Hardware Tokens
Hardware tokens, such as YubiKey or other USB/NFC devices, provide a physical second factor for authentication. These small devices generate or store secure authentication keys that must be physically present to access your account. This method offers a very high level of security since hackers cannot remotely access your hardware token, making it almost immune to phishing or hacking attempts. Hardware tokens are widely used by security-conscious users and organizations.
How to Set Up Two-Factor Authentication on Popular Platforms
Setting Up 2FA on Google Account
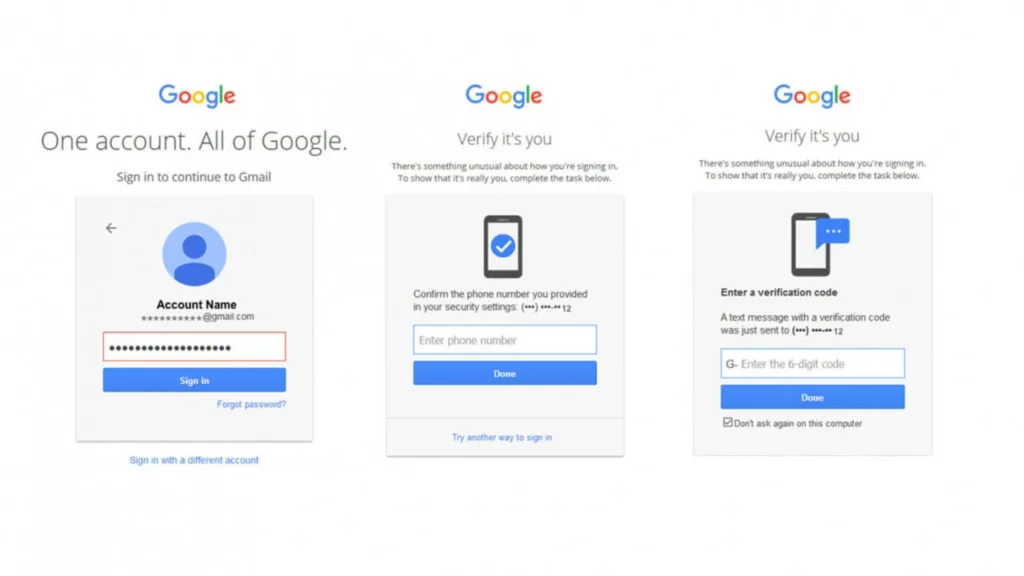
Google offers robust support for two-factor authentication to protect your Gmail and other Google services. To enable it, log in to your Google Account and navigate to the “Security” section. From there, select “2-Step Verification” and follow the prompts to add a phone number for SMS codes or set up an authentication app like Google Authenticator. You can also add backup options such as backup codes or security keys to ensure continued access if your primary device is unavailable.
Enabling 2FA on Facebook and Instagram
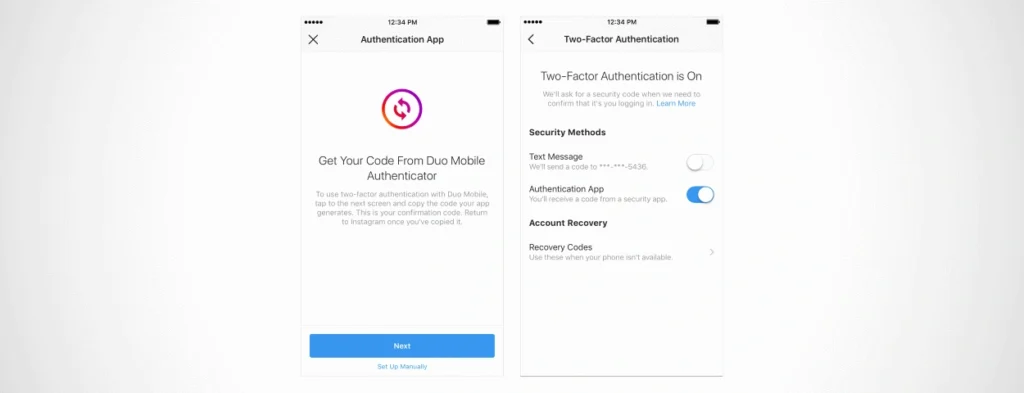
Both Facebook and Instagram, owned by Meta, provide similar 2FA setups. To enable it, go to your account settings on either platform, find the “Security and Login” section, and click on “Two-Factor Authentication.” You can then choose to receive codes via SMS, use an authentication app, or set up a security key. These options help safeguard your social media accounts from unauthorized access, especially since they often contain personal information and contacts.
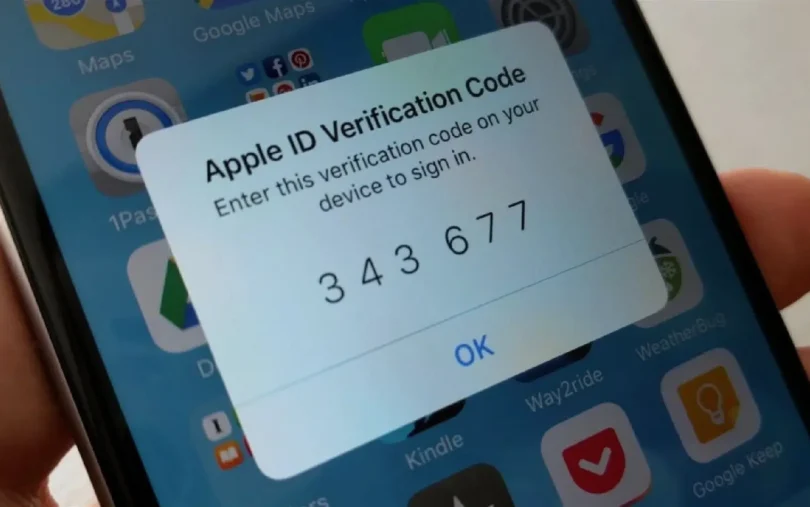
Activating 2FA on Your Apple ID
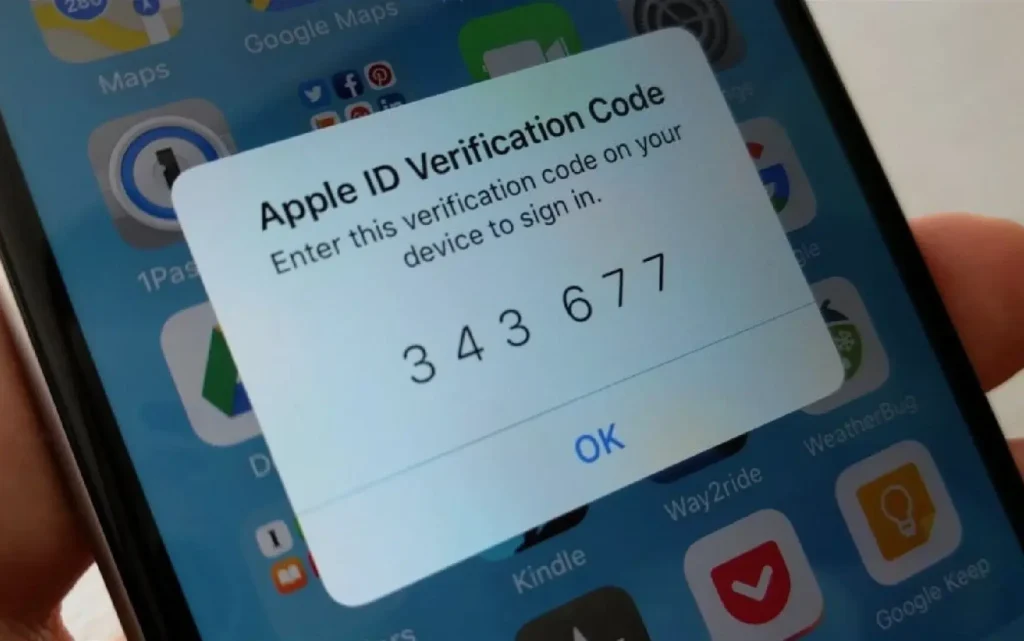
Apple users can secure their Apple ID, which controls access to iCloud, App Store, and other Apple services, by enabling two-factor authentication. On your iPhone or iPad, go to Settings > [your name] > Password & Security. Tap “Turn On Two-Factor Authentication” and follow the instructions to link your trusted phone number or device. Apple’s 2FA setup often includes sending verification codes directly to your trusted devices, enhancing both security and convenience.
Best Practices for Using Two-Factor Authentication Securely
Backup Codes: What They Are and Why You Need Them
Backup codes are a set of one-time-use codes provided by many services when you enable 2FA. These codes act as a safety net, allowing you to access your account if you lose your phone or cannot receive authentication codes. It’s crucial to download, print, or securely store these backup codes in a safe place because without them, you risk being locked out of your accounts if your primary 2FA method fails.
Avoiding Phishing Scams and Fake 2FA Prompts
While 2FA significantly enhances security, attackers sometimes try to trick users into revealing their second-factor codes through phishing scams. Always verify the authenticity of login prompts and avoid entering your 2FA code on suspicious websites or apps. Genuine services will never ask you for codes via unsolicited emails or messages. Staying vigilant and skeptical helps protect you from social engineering attacks targeting your two-factor authentication.
Using Strong Passwords Alongside 2FA
Two-factor authentication is a powerful security layer, but it should never replace a strong password. Always use complex, unique passwords for each of your online accounts. Combining strong passwords with 2FA drastically reduces the chances of unauthorized access. Consider using a reputable password manager to generate and store strong passwords, making your security setup both robust and manageable.
Conclusion
Implementing a Two-Factor Authentication Setup Guide is one of the most effective ways to protect your online accounts from unauthorized access. By adding that extra verification step, you significantly reduce the risk of your personal data being compromised, even if your password falls into the wrong hands. Whether you choose SMS codes, authentication apps, or hardware tokens, enabling 2FA on your key accounts like Google, Facebook, and Apple ID is essential in today’s digital landscape. Remember to follow best practices such as securely storing backup codes, staying alert against phishing attempts, and maintaining strong passwords. Taking these steps will give you greater peace of mind and a stronger defense against cyber threats.